The Rise of Ransomware: Trends and Mitigation Strategies
| By Uday Annavarapu |
Ransomware Attacks a Growing Challenge for Organizations Worldwide
Ransomware attacks have surged dramatically over the past decade, becoming one of the most prevalent and damaging forms of cybercrime. In these attacks, malicious entities encrypt a victim’s data and demand a ransom for release. These attacks have targeted various industries, including healthcare, finance, and critical infrastructure. As ransomware evolves in complexity and scale, understanding its trends and implementing effective mitigation strategies is crucial for organizations worldwide.
The Evolution of Ransomware Threats
Ransomware gained prominence in the early 2000s with simple attacks that often targeted individual users. Over time, these attacks have grown more sophisticated, with the emergence of ransomware-as-a-service (RaaS) platforms enabling even low-skilled cybercriminals to launch attacks. Modern ransomware groups are well-organized, often operating like legitimate businesses with customer support and negotiation teams.
The Cybersecurity and Infrastructure Security Agency shed light on the recent rise of double extortion techniques, where attackers encrypt data and threaten to leak sensitive information, adding another layer of pressure on victims. This evolution in tactics has contributed to the increase in the frequency and severity of ransomware incidents, making it one of the most formidable challenges in cybersecurity today.
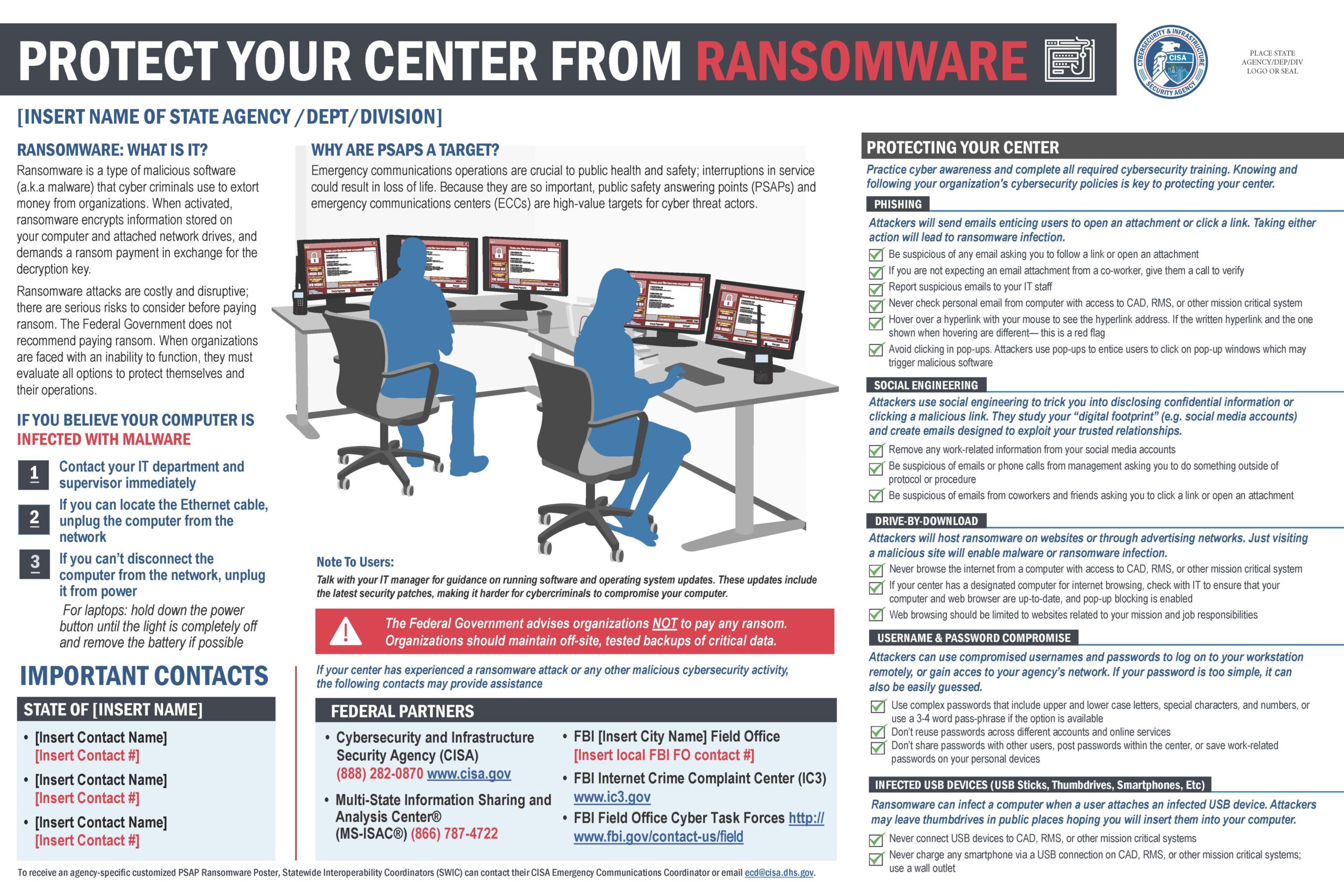
Critical Trends in Ransomware Attacks
Ransomware attacks have evolved significantly in recent years, posing increasing challenges to global security. Cybercriminals have increasingly targeted critical infrastructure, including energy grids, transportation networks, and healthcare systems. The Colonial Pipeline attack in 2021 is a notable example, where a ransomware attack led to widespread fuel shortages across the Eastern United States.
Another worrying development is the exploitation of third-party vendor and supplier vulnerabilities to gain unauthorized access to larger organizations. The 2020 SolarWinds attack showed how supply chain vulnerabilities can be leveraged for ransomware deployment on a significant scale.
The anonymity provided by cryptocurrencies like Bitcoin has facilitated ransomware’s growth. The anonymity afforded by these digital currencies allows attackers to receive payments without revealing their identities, emboldening them and fueling the growth of the ransomware industry.
Furthermore, the emergence of Ransomware-as-a-service platforms has made it easier for aspiring cybercriminals to enter the realm of ransomware attacks. The platforms provide pre-built ransomware tools to affiliates, who then execute attacks and share the profits with the platform operators. This model lowers the barriers to entry and has led to a proliferation of ransomware activity.
Mitigation Strategies for Ransomware
In the face of the growing threat posed by ransomware attacks, organizations must remain vigilant and proactive in implementing comprehensive mitigation strategies. By adopting a multi-faceted approach encompassing secure data backup protocols, robust network segmentation, and meticulous incident response planning, businesses can significantly enhance their resilience against these ransomware cyber threats.
The Center for Internet Security emphasizes that maintaining regular, secure backups of critical data is one of the most effective ways to reduce the impact of a ransomware attack. By storing these backups offline and conducting frequent tests to ensure their quick restoration during an attack, organizations can significantly bolster their defenses against potential data loss.
Moreover, implementing robust network segmentation practices can serve as an effective barrier to contain the spread of ransomware within an organization’s IT infrastructure. By strategically isolating critical systems and data, companies can prevent attackers from gaining unfettered access to their entire network, thereby limiting the scope of potential damage.
Complementing these measures, the National Cyber Security Centre stresses the importance of incident response planning in mitigating ransomware attacks. A clear incident response plan is essential to minimize the impact of a ransomware attack. Developing and regularly updating a clear, actionable incident response plan is indispensable in minimizing the disruption caused by such cyber threats. A well-crafted strategy empowers organizations to swiftly identify, contain, and recover from ransomware incidents, ultimately safeguarding their operations and reputation.
The Path Forward: Embracing Proactive Cybersecurity Measures
By staying informed about the latest trends and adopting comprehensive mitigation strategies, organizations can reduce their vulnerability to these attacks. As the technological landscape changes, maintaining vigilance and adaptability will be vital to defending against ransomware. Staying abreast of emerging trends and swiftly implementing comprehensive mitigation strategies are not mere advantages—they are imperatives for safeguarding valuable assets and ensuring business continuity in an increasingly digital world.
Photo Credits: CISA



